Default Password Bizhub 4020i: Comprehensive Reset & Admin Access Guide
Learn how to identify and disable default passwords on the Bizhub 4020i, reset the administrator password, and implement security best practices for printers in 2026.

The Bizhub 4020i security posture hinges on eliminating default credentials and setting unique admin access. This guide provides a concise overview: verify if a default admin account exists, reset the password securely, and enforce ongoing access controls. By following vendor recommendations and best practices in 2026, you reduce the risk of unauthorized printer configuration changes and data exposure.
Understanding the risk of default passwords in printers
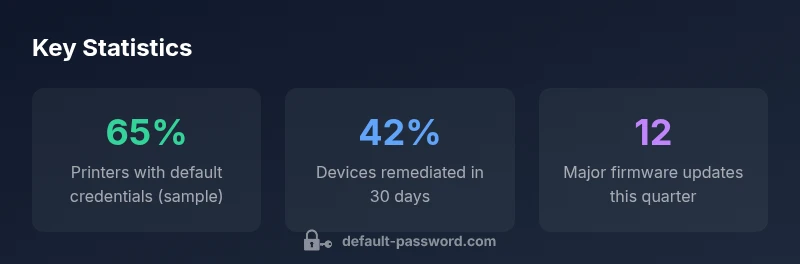
Office printers, including the Bizhub 4020i, often ship with default administrator accounts to simplify initial setup. While convenient, these defaults present a persistent security risk if left unchanged. Attackers increasingly target networked devices with web interfaces and management consoles to pivot into broader networks. In 2026, security teams emphasize credential hygiene as a foundational control for printers, copiers, and multifunction devices. A strong password discipline—paired with disabling or rotating default accounts—reduces the attack surface and helps organizations meet security baselines and regulatory expectations. Early risk assessments should include a quick inventory of all printers, confirm the presence of administrator accounts, and verify that default passwords have been changed.
Key concepts to remember: default credentials, admin access, printer security, credential hygiene, and least privilege. As you audit devices, plan a practical rollout that aligns with your organization’s risk tolerance and IT policy requirements.
Bizhub 4020i specifics: default credentials landscape and vendor guidance
Konica Minolta’s Bizhub models historically require administrative access for configuration changes. The Bizhub 4020i falls into this pattern where an initial login is needed to set up scan, print, and network features. Vendor guidance typically stresses changing any factory-default credentials during the first login and enabling security features such as TLS, account locking, and regular firmware updates. While exact default credentials can vary by firmware version and regional builds, the overarching message is consistent: do not rely on the default admin password. Security teams should treat Bizhub devices as high-priority assets requiring explicit credential management, network segmentation, and periodic configuration reviews. This approach reduces exposure to unauthorized configuration changes and preserves auditability.
How to check the current password configuration on Bizhub 4020i
To assess your current security posture, start by locating the device’s management interface. Access can occur via the built-in LCD panel or the web UI using the printer’s IP address. Look for sections labeled Security, Administrator Settings, User Management, or Access Control. If you see a named admin account with a blank or known default password, you should plan an immediate password change. Document the existing configuration, note any disabled default accounts, and verify whether two-factor authentication or strong password policies are enforced. For multi-device fleets, run a centralized audit to compare configurations and identify outliers. If you cannot access the UI due to locked credentials, you may need to perform a controlled reset per vendor guidance, ensuring service windows and data preservation plans are in place.
Step-by-step: Reset admin password on Bizhub 4020i
Resetting the admin password should be done carefully to avoid losing device functionality. General steps include: (1) Note the current IP address or connect locally to the device. (2) Access the management interface or service mode as documented by the vendor. (3) Choose the option to reset the administrator password or perform a factory reset for security-critical breaches. (4) Reboot the device and verify access with the new credentials. (5) Immediately reconfigure security settings and disable any legacy accounts. Always refer to the official Bizhub 4020i manual for exact steps and prerequisites before performing resets, and ensure backups and network credentials are considered in the plan.
Post-reset hardening: policies, password length, and rotation
After resetting, implement a robust hardening plan. Enforce long, complex passwords (14+ characters with a mix of upper/lowercase, numbers, and symbols), rotate credentials on a defined cadence, and remove any unused administrator accounts. Enable account lockout after repeated failed attempts, audit login events, and restrict admin access to trusted network segments. Document changes in a change-management system and communicate policy updates to IT staff. Consider integrating printer credentials with a centralized password-management solution where possible, and maintain firmware update schedules to address known vulnerabilities.
Firmware updates and access controls: ensure resilience
Firmware updates are a critical line of defense for printers like the Bizhub 4020i. Keep the device on a current release, verify signatures, and schedule updates during maintenance windows. Implement access controls that limit management interfaces to trusted devices and users, disable unnecessary features (such as remote administration if not required), and ensure secure protocols (HTTPS, TLS) are enforced. Regularly review access logs, enable encryption for stored credentials where supported, and align with organizational security baselines to reduce exposure from misconfigured or outdated firmware.
Practical examples and common pitfalls
Common pitfalls include delaying password changes after deployment, using weak or reused passwords across devices, and neglecting fleet-wide credential hygiene. Practical examples involve failing to disable a default admin account on one printer, which can create a foothold for lateral movement in the network. A proactive approach includes scheduling quarterly credential reviews, verifying that all admin accounts are unique and active, and maintaining an up-to-date inventory of devices with their respective access configurations. Anticipate recovery needs by documenting reset procedures and ensuring authorized personnel can perform resets during incidents.
Documentation and audit trails: recording changes and compliance
Keep a centralized log of all credential changes, resets, and policy updates. Audit trails support incident response, compliance reporting, and security program maturity. For the Bizhub 4020i, maintain records of when admin passwords were changed, who performed the change, and the device’s current security posture. Regular reviews help identify drift from policy and provide evidence during audits or regulatory reviews. Pair documentation with automated alerts for unusual login activity and configuration changes to stay ahead of potential threats.
Printer security posture for Bizhub 4020i and related devices
| Device | Default Credential Status | Recommended Action |
|---|---|---|
| Bizhub 4020i | unknown/varies by firmware | Verify official docs and change to unique credentials; enforce password policy |
| Printer fleet (office devices) | unknown | Implement organization-wide password policy and rotate credentials |
| Network printers (general) | some devices use default admin accounts | Disable or change default accounts; enforce least privilege and logging |
Your Questions Answered
What is the Bizhub 4020i default admin password?
Default passwords vary by firmware version and region; many Bizhub devices ship with an administrative account that should be changed on first login. Always consult the official documentation or vendor support for the exact credentials for your device.
Default passwords vary by firmware and region; check the official Bizhub docs to confirm the right credentials before proceeding.
How do I reset the Bizhub 4020i administrator password?
Reset procedures differ by firmware and network setup. Use the device’s management interface or service mode to reset, then immediately create a new strong password and reconfigure security settings as recommended by the vendor.
Use the device interface or service mode to reset, then set a strong new password and tighten security settings.
What are best practices after resetting the admin password?
Implement a policy requiring long, unique passwords, enable account lockout, rotate credentials regularly, and document changes in your security governance processes. Review firmware and enable secure protocols.
Use a long, unique password, enable lockout, rotate credentials, and keep firmware up to date.
Can I recover a forgotten admin password on Bizhub 4020i?
If you cannot access the admin account, consult vendor support for recovery or a controlled reset process. Do not bypass security controls; follow approved incident procedures to regain access.
If you’re locked out, contact vendor support for a legitimate recovery or reset procedure.
Are there risks in using default passwords?
Yes. Default passwords create an easy entry point for attackers, enabling unauthorized changes and data exposure. Harden printers by changing credentials, restricting access, and keeping firmware updated.
Defaults are risky—change them, restrict access, and keep firmware updated.
“Security hinges on removing default passwords across devices; proactive credential hygiene is essential for printer security.”
Key Takeaways
- Audit all office printers for default credentials
- Change admin passwords immediately on first login
- Enforce strong, unique credentials and rotation policies
- Disable unused accounts and enable logging