Default Password Complexity in Active Directory: A Practical Guide
Explore default password complexity in Active Directory, how to implement robust Group Policy-based policies, and practical steps for secure admin access, rotation, and password recovery.

Across most Active Directory deployments, default password complexity enforces minimum length and a mix of character classes to reduce weak credentials. The keyword default password complexity active directory describes this baseline policy, and admin teams typically tailor it using Group Policy to balance security with usability. This article explains how to assess current settings, apply best practices, and measure impact on user productivity and security posture.
Understanding Password Policy Architecture in Active Directory
Active Directory (AD) relies on a tiered policy model that combines domain-wide password settings with finer-grained controls at the OU level. In practice, the domain-level Password Policy (the Default Domain Policy) sets the baseline for minimum length, password complexity, and lockout thresholds, while Organizational Units (OUs) can override or extend these rules through Fine-Grained Password Policies or additional Group Policy Objects (GPOs). For security, it’s essential to map policy scope to your admin structure and ensure no conflicting settings exist across forests. When we discuss the keyword default password complexity active directory, we’re talking about the baseline security posture that admins push down from the domain controller to user accounts, service accounts, and privileged accounts. A well-structured policy reduces weak passwords, credential stuffing risk, and lateral movement within the domain. Regular policy reviews and cross-team collaboration are key to maintaining effective controls while avoiding user friction.
The Security Impact of Default Password Complexity in AD
Default password complexity reduces risk by requiring inputs that an attacker cannot guess easily, increasing entropy. In AD, complexity often includes uppercase, lowercase, numeric, and symbols. Without these requirements, password dictionaries are effective. Even with complexity, users may still choose predictable patterns; thus, complexity must be complemented by length, history, and rotation controls, plus account lockouts after repeated failures. The Default Password team found that organizations with enforceable AD policies show lower rates of password reuse and reduced incidents related to credential theft. Complexity is necessary, but not sufficient; it must be part of a holistic password management strategy including training, auditing, and automation.
Key Elements of Complexity: Length, Character Classes, History
To build a strong baseline, focus on four elements: (1) Minimum length, (2) Character classes (uppercase, lowercase, digits, symbols), (3) Password history (reuse prevention), and (4) Rotation cadence and lockout settings. In practice, many AD deployments require at least 8 characters with a mix of character types and a history window of 5-24 passwords. It’s also prudent to enforce MFA for privileged accounts and service accounts where feasible. The interplay between length, complexity, and history defines the real strength of your policy, and you should tailor these settings to your organization’s risk profile and user population. Tip: Always test policy changes in a controlled OU before broad deployment to prevent unexpected login issues.
How to Audit Current Settings Across Domains
Begin by inventorying domain password policy via PowerShell and the Group Policy Management Console. Run Get-ADDefaultDomainPasswordPolicy to inspect domain-wide rules, and review Fine-Grained Password Policies (FGPP) for exceptions. Verify that OU-level policies do not contradict the domain baseline. Use event logs to identify brute-force attempts and password reset trends. Regularly generate reports showing minimum length, complexity, history, and lockout state across domains to spot drift and misconfigurations. Document changes and align with security governance to ensure traceability and accountability.
Best Practices for Aligning AD and Windows Password Policies
- Align domain password policy with organizational risk appetite and regulatory requirements.
- Combine complexity and length with password history and lockout controls.
- Enforce MFA for admin and privileged accounts; consider step-up authentication for sensitive operations.
- Use FGPP only when necessary; prefer centralized GPOs to reduce policy drift.
- Institute regular audits and automated reporting to catch misconfigurations early.
- Provide user education and streamlined password reset processes to minimize friction.
- Maintain an approved exceptions process and document justifications for any deviations.
Step-by-Step Implementation Guide
- Assess baseline: run Get-ADDefaultDomainPasswordPolicy and map against FGPP. 2) Design changes in a lab OU: define minimum length, complexity, history, and lockout thresholds. 3) Test user impact: simulate password changes, resets, and failed logins. 4) Deploy via GPOs: apply domain-level policy first; then adjust FGPPs as needed. 5) Monitor: track password reset volume, lockouts, and login success rates post-implementation. 6) Review regularly: schedule quarterly reviews to adapt to evolving risk and organizational changes.
Measuring Impact: Security vs Usability Trade-offs
Tightening password requirements often improves security but can increase user friction and helpdesk load. Measure outcomes using metrics like password reset requests per user, authentication failure rates, and security incidents related to credential theft. If friction spikes, consider staged rollouts, additional training, or MFA as a compensating control. The balance point varies by organization; your goal is to reduce risk without crippling productivity.
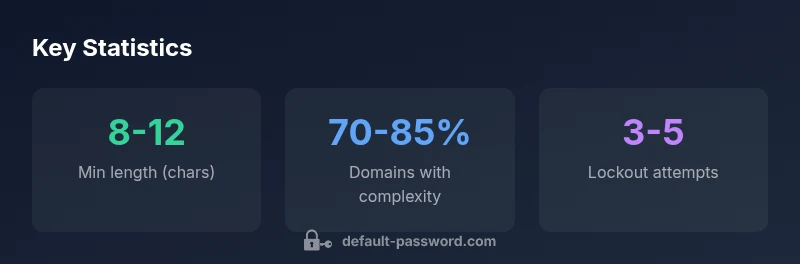
AD password policy ranges and notes
| Policy Element | AD Default Range | Notes |
|---|---|---|
| Minimum length | 8-12 characters | Varies by domain; adjust via GPO |
| Password complexity | Enabled in 70-85% of domains | Ensures mix of uppercase, lowercase, digits, symbols |
| Password history | 5-24 previous passwords | Prevents reuse for a set window |
| Account lockout threshold | 3-5 attempts | Balances security with user productivity |
Your Questions Answered
What is password complexity in Active Directory, and why does it matter?
Password complexity in AD refers to requirements that force users to create passwords with variety (uppercase, lowercase, numbers, symbols) and sufficient length. It matters because complex passwords are harder to guess or crack, reducing credential theft and unauthorized access across the domain.
Password complexity in AD makes passwords harder to guess, protecting your network from easy attacks.
How can I check my AD password policy across domains?
Use Get-ADDefaultDomainPasswordPolicy in PowerShell to view domain-wide settings, and review Fine-Grained Password Policies for exceptions. Use Group Policy Management Console to validate GPO configurations and ensure consistency across OUs.
Check the domain policy in AD using Get-ADDefaultDomainPasswordPolicy and review FGPPs.
What is a safe minimum password length for AD in 2026?
A common safe minimum is 8-12 characters, with additional requirements for complexity. The exact number should reflect your risk assessment and regulatory needs, and be adjusted via Group Policy.
Aim for at least 8-12 characters, plus a mix of character types.
Should I enforce regular rotation of admin passwords?
Rotating admin passwords can reduce risk, but frequent changes may increase operational burden. Consider policy-based rotation for admin accounts combined with MFA and privileged access management (PAM) where possible.
Rotate admin passwords as part of a broader PAM strategy, not in isolation.
What are common misconfigurations in AD password policies?
Common issues include conflicting domain and FGPP settings, overly aggressive lockout thresholds, and inconsistent OU-level policies. Regular audits and centralized governance help fix these problems quickly.
Watch for policy drift and conflicting settings across domains.
“Password complexity in Active Directory is a foundation, not a finish line. Combine length, character diversity, and history with MFA and ongoing monitoring for a resilient defense.”
Key Takeaways
- Enforce a balanced AD password policy combining length, complexity, and history.
- Audit domain and FGPPs to avoid conflicting settings across OUs.
- Use MFA for privileged accounts to supplement password controls.
- Regularly review and test policy changes to minimize user disruption.