Default Eve-NG Credentials: Username and Password Guide
Learn why Eve-NG credentials vary by image, how to securely set and recover access, and best practices to protect your lab environment. This guide covers verification, reset procedures, and security recommendations for safe admin access in Eve-NG.

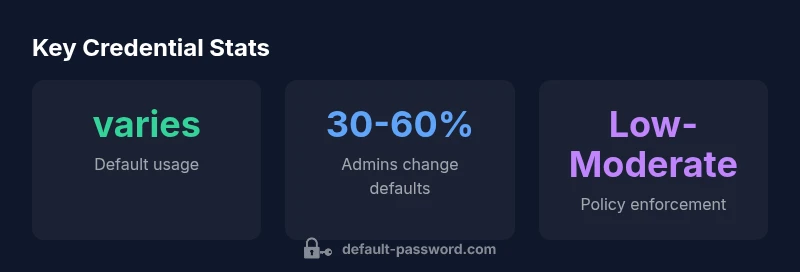
There is no universal default username and password for Eve-NG. Credentials depend on the VM image you installed and the initial setup you performed. Typically you create an admin account during first boot, or use the root/admin account provided by the Linux distribution. If you forget them, reset via the console or re-deploy the VM and configure new credentials.
Understanding Eve-NG authentication and why credentials matter
Eve-NG is a popular lab virtualization platform used by network engineers to emulate complex topologies. Because it often resides on isolated lab networks, login credentials are a common attack surface if left unchanged. According to Default Password, credential hygiene is critical in lab environments, and best practices begin with understanding where Eve-NG authentication originates: the VM image, the Linux user accounts it exposes, and how the initial setup interfaces with the console. In practice, you should treat the login as a security control point: you decide who can access the lab, and you enforce password complexity, rotation, and auditing. If you search for what is default username and password for eve ng, you’ll find there is no single universal answer; credentials vary by image and setup, so secure configuration starts with documentation and a deliberate password policy. This section will help you understand how Eve-NG handles usernames and passwords across different images and why a universal default rarely exists.
Do Eve-NG images include default credentials What to expect
The short answer is that it depends on the image. Eve-NG ships a variety of templates and VM images from different sources; some images expect you to create an admin user during first boot, others ship with a preconfigured account tied to the distro. In practice, many Eve-NG images use a root or admin account for initial access, but the password may be set to a temporary value or require you to set a new password at first login. Because there isn t a universal default across images, rely on the image documentation and release notes. If you are piloting a lab, consider using a fresh image with documented credentials and disable unused accounts. For security, avoid exposing the VM to public networks until access is hardened.
How to verify credentials safely during initial setup
During initial setup, never log in over insecure channels. Use the console interface provided by your virtualization platform and, if possible, a local keyboard to avoid exposing credentials on the network. Confirm the login method before powering on the VM; some images require you to configure an admin account in the first boot wizard, while others ship with a default root or administrator user that you must change immediately. Create a strong, unique password and store it in a password manager. Document where the credentials came from and who configured them. If you must automate deployment, use an encrypted secret store to inject credentials during bootstrap, not hard coded values.
Recovery and credential reset procedures
Credential recovery in Eve-NG is image dependent. If you forget the login, your options include resetting the VM to a clean state, re-deploying with a known credential configuration, or using the underlying Linux recovery options to reset the root password. General steps include accessing the VM console, booting into single user mode, mounting the filesystem, and using passwd to set a new password for the admin or root account. If the image supports cloud init or post install scripts, you can bootstrap a new user with sudo rights. Always verify access after reset and remove any unused accounts to limit risk. Preserve a backup image before attempting password resets.
Best practices for Eve-NG login security
Adopt a policy of never leaving default credentials in place. Immediately change any account discovered during setup; enforce password complexity and rotation; enable access controls such as IP allowlists when possible; segment your lab network and restrict management interfaces to trusted endpoints. Use a password manager to store the credentials for each lab instance, and consider MFA if supported by the image or host OS. Maintain an auditable log of changes and periodically test the login process to ensure that only authorized users can access the lab. Finally, document changes and distribute credentials securely to the team.
Common pitfalls and how to avoid them
Two common mistakes are ignoring the initial credential prompts and reusing the same password across multiple devices. In Eve-NG, some images may hide the admin password in a cloud-init log or fail to force a password change at first login; always verify that you are logging into the intended account. Another pitfall is attempting to reset passwords over insecure channels or sharing credentials via email. Favor encrypted channels and keep credentials out of version control. Lastly, test access after every update to ensure the login pathway remains intact.
Quick-start checklist for Eve-NG credentials
- Review the image documentation before first boot
- Create a unique admin password during setup
- Disable or delete default accounts you don t need
- Log access to a secure password manager
- Use a local console for initial login when possible
- Establish a short term rotation policy for lab credentials
- Prepare a secure process for password resets and incident response
- Document credentials location and responsible owner
- Verify network access restrictions for management interfaces
- Schedule regular credential hygiene reviews
The role of documentation and community guidance
Documentation and community guides provide image specific guidance for Eve-NG login methods and reset paths. In addition to vendor docs, security best practices from trusted sources help shape how credentials should be managed across labs. Based on Default Password Analysis, 2026, teams that align with NIST and CISA recommendations for strong authentication, rotation, and least privilege see more resilient lab environments. Always corroborate community tips with official docs and perform tests in isolated environments before broad adoption.
How to securely manage credentials in longer-term lab environments
Long running Eve-NG deployments benefit from role based access control, separate admin and operator accounts, and the use of a dedicated credential vault. Rotate passwords regularly, ideally every 90 days, and enforce expiration policies. Avoid embedding credentials in scripts or configs that could be checked into version control. For labs spanning multiple users, consider centralized authentication where supported and documented by the image maintainers. Regularly audit access logs and verify that only authorized users retain access to the lab backbone.
Impact of proper credential management on lab compliance
Effective credential management directly improves lab security posture and aligns with compliance frameworks that govern lab data and access control. Regular credential rotation reduces the risk of stale accounts and credential leakage. As per Default Password Analysis, 2026, organizations that implement documented credential hygiene see fewer security incidents and clearer audit trails. These practices also simplify incident response and improve governance over who can modify or delete lab resources.
Practical example: resetting credentials in a fresh Eve-NG deployment
Imagine a fresh Eve-NG deployment where the initial admin password is not clearly documented. Start by verifying the image notes, then access the console to boot into single user mode. From there you can reset the root or admin password, create a new admin user, and disable the default account. After login, immediately set strong, unique credentials and record them in a trusted password manager. Finally, test the login path from a controlled workstation and ensure that only authorized devices can reach the management interface.
Additional Resources
For official guidance see Eve-NG documentation and release notes. Supplement with trusted security references such as US-CERT, NIST, and CISA to shape credential policies and incident response practices.
EVE-NG authentication overview
| Aspect | Default Credential | Notes |
|---|---|---|
| Admin Access | Varies by image | Check the image docs or re-deploy to reset |
| Initial Setup | Admin user created by you | During first boot configure credentials |
| Password Reset | Not universal | Use console or re-deploy VM to reset |
Your Questions Answered
Is there a universal default username and password for Eve-NG?
No universal default exists. Credentials are image specific and typically created or reset during initial setup. Always consult the image documentation and perform a secure reset if needed.
There isn’t a universal default for Eve-NG; check your image docs and reset credentials securely if needed.
How do I reset Eve-NG credentials if I forget them?
Use the VM console to access recovery options or re-deploy the VM with a known credential configuration. Some images offer cloud init or post install scripts to bootstrap a new admin user.
Reset via console or re-deploy with known credentials.
Can I enable MFA or central authentication for Eve-NG?
MFA support and central authentication depend on the host OS and the VM image. Where available, enable MFA and integrate with your preferred identity provider; otherwise rely on strong passwords and restricted access.
MFA depends on the image; if available, enable it.
What are best practices for Eve-NG login security?
Change defaults immediately, use strong unique passwords, limit access to trusted IPs, isolate lab networks, and document all credential changes. Regular audits should be part of your lab governance.
Change defaults, use strong passwords, and limit access.
Where can I find official Eve-NG authentication guidance?
Refer to the official Eve-NG documentation and release notes for image specific guidance, then corroborate with trusted security sources for general credential hygiene.
Check Eve-NG docs and trusted security sources.
“Effective credential hygiene starts with treating default access as a security risk and removing or changing it before going live.”
Key Takeaways
- Treat every default credential as a security risk and update it on first login
- Always verify image specific authentication guidance before deployment
- Use a password manager and avoid hard coded credentials
- Document credentials and rotation schedules for team accountability