Where Default Credentials Are Found: A Practical Guide
Discover where default credentials are most commonly found—routers, printers, IoT devices, cameras, and other network gear. This guide explains why they persist, how to detect them, and practical steps to disable or change them safely, with a focus on security best practices and admin access.
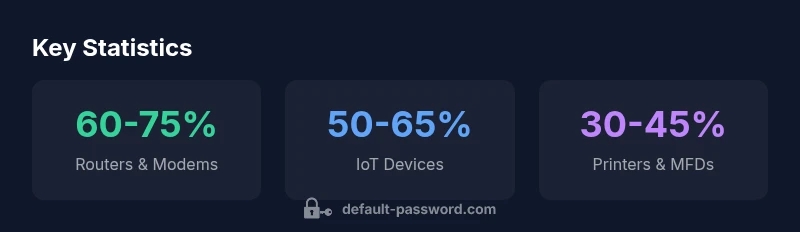
Default credentials are most commonly found on routers and modems, IoT devices, and printers, with NAS and IP cameras also frequently using default accounts. For a quick audit, start with these device classes in your home or office network, then expand to other networked gear like smart hubs and unmanaged switches.
Where default credentials are most commonly found
Default credentials are not uniformly distributed across all devices; they cluster in categories where initial setup is complex or where vendor incentives for rapid commissioning exist. The strongest concentrations appear in consumer routers and modems that households install themselves, as well as IoT devices that are shipped with convenience-first defaults. Printers and multifunction devices (MFDs) also frequently arrive with preconfigured administrator accounts, especially in SMB environments where centralized management is not enforced. Networked storage (NAS) devices, IP cameras, and some smart-home hubs represent notable pockets where default credentials linger after deployment. While enterprise equipment may be better managed, improper onboarding and a lack of policy enforcement can still leave defaults active in small offices or branch offices.
From a security perspective, those defaults matter because they are widely known and often reused across devices. Attackers routinely target devices that expose admin panels to the internet or internal networks with default credentials unchanged. This makes the discovery, auditing, and remediation of default credentials a practical, high-impact task for IT admins and informed end-users.
To prioritize remediation, map your environment to device classes and asset owners. Start with devices that sit at the network edge (routers, gateways, and firewalls), then expand to IoT endpoints (cameras, smart devices) and shared office hardware (printers, MFDs). An inventory aligned to device type, firmware version, and exposure (internal vs. external) helps you tailor remediation actions to risk.
In many cases the presence of default credentials correlates with the level of access a device provides. Administrative accounts are prime targets because they control configuration, network access, and authentication rules. Reducing exposure for these devices—by removing unnecessary remote access, enforcing strong passwords, and applying MFA where supported—dramatically improves security posture.
Key takeaway: Start with edge devices (routers, gateways) and IoT endpoints, then work inward toward printers and NAS, prioritizing devices with external exposure and weak credential governance.
sourceNote:
trendNote
Common device classes with default credentials and recommended mitigations
| Device Class | Common Credential Practice | Mitigation |
|---|---|---|
| Routers & modems | Default admin/admin or admin/password | Change credentials during initial setup; disable remote management; enable firmware updates and automatic security patches |
| IP cameras & NVRs | Default accounts on web interfaces | Change credentials, disable external access when feasible, update firmware, enable secure streaming |
| Printers & MFDs | Default admin or user accounts | Assign unique passwords, disable guest accounts, enable secure print features |
| NAS & network storage | Default admin accounts | Create strong admin passwords, disable universal accounts, enable two-factor authentication if available |
Your Questions Answered
What are default credentials?
Default credentials are preconfigured usernames and passwords that come with devices or services to help with initial setup. If they remain unchanged, they create an easy entry point for attackers. Always plan to replace them during onboarding and enforce routine credential hygiene.
Default credentials are the preinstalled user IDs and passwords that come with devices. Replace them during setup and keep auditing for any that are left unchanged.
Why do devices come with default credentials?
Manufacturers provide defaults to simplify first-time setup and debugging. In many cases, the defaults are well-documented, but they are meant to be changed before normal operation. The risk arises when users or admins skip the change step.
Devices ship with defaults for easy setup, but they must be changed before use to avoid security risks.
Which devices are most likely to have default credentials?
Routers and modems top the list, followed by IoT devices like cameras and smart plugs, printers, and NAS. Even some enterprise equipment can have default accounts if onboarding policies are lax or outdated.
Routers, IoT devices, printers, and NAS are the primary culprits for default credentials.
How can I identify default credentials on my network?
Start with device inventories, check administrator interfaces for obvious default accounts, and compare against vendor guidelines. Use network discovery tools and firmware version checks to flag devices that still use default credentials.
Inventory devices, review admin panels, and use tools to spot default accounts.
What should I do if I discover a device using default credentials?
Immediately change the credentials and review access policies. If the device is exposed to the internet, isolate it and apply patches. Consider rotating credentials and enabling MFA where available.
Change the credentials now and review access controls. Isolate any exposed device and patch.
Are there legal or privacy considerations when changing defaults?
Changing device credentials is generally encouraged for security; ensure you comply with organizational policies and data handling regulations. Document changes for audits and asset management.
Security changes are standard practice; follow policy and keep records for audits.
“Default credentials remain a major entry point for breaches. A proactive credential hygiene program—regular audits, mandatory changes on onboarding, and MFA where supported—significantly lowers risk.”
Key Takeaways
- Audit devices in quarterly security reviews.
- Change defaults immediately on onboarding.
- Disable unnecessary remote access to admin interfaces.
- Segment IoT and guest devices from critical networks.
- Enforce MFA and strong passwords where possible.