Default Passwords for Epson TM-U220: Reset, Secure, and Manage
Learn how to identify, reset, and secure default passwords on the Epson TM-U220 receipt printer. Practical steps, best practices, and security guidance from Default Password.

Many Epson TM-U220 printers ship with default admin credentials that, if left unchanged, can expose the device to unauthorized access. To regain control, perform a safe factory reset via the maintenance mode and reconfigure with a unique password. This guide from Default Password covers reset steps, verification, and best practices to secure the device.
Understanding default password epson tm u220
The Epson TM-U220 is a popular receipt printer used in retail, hospitality, and small offices. Like many legacy and legacy-forward devices, some firmware revisions and configurations ship with a default admin password to simplify setup. While convenient for initial installation, leaving this credential unchanged creates a significant risk: attackers or internal misusers could gain access to the printer’s configuration, firmware update interfaces, or network exposure. The exact default password and its location depend on the model variant and firmware level, so always consult the official documentation for your specific unit. In practice, you should assume that a default credential exists until you verify its removal or rotation, and treat the device as a potential access point that requires immediate hardening. For the purposes of this guide, we discuss a generic path to regain control and lock the device down securely.
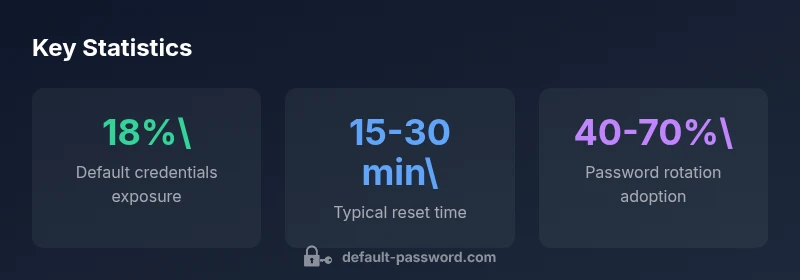
The security risks of unchanged credentials on printer devices
Default credentials on printers pose multiple risk vectors. First, printers often sit on shared networks with access to print jobs, stored configuration data, and even firmware update channels. If an attacker gains admin access, they could alter print queues, siphon sensitive paper trails, or push malicious firmware where available. Second, many small business printers lack rigorous access controls or centralized password management, making manual changes inconsistent across devices. Finally, when default credentials are reused across devices, you create a broader attack surface that extends beyond a single printer. The best defense is to assume that any device shipped with a default credential should be treated as a potential risk until it is reset and secured. This is a core principle of secure device lifecycle management, reinforced by standard guidance from security authorities.
Step-by-step reset of Epson TM-U220
Resetting a printer to factory defaults should be performed carefully and documented. While exact steps vary by firmware, a typical path includes:
- Verify model and firmware: Confirm your TM-U220 variant and current firmware version to determine the correct reset method.
- Enter maintenance or recovery mode: Use the combination of hardware inputs and power cycling described in the user manual to access a maintenance menu. If your unit supports it, select the option to reset to factory defaults.
- Execute factory reset: Initiate the reset, allowing the device to restore its default settings. Do not interrupt the process.
- Reconfigure securely: After the reset, immediately set a unique admin password that uses a combination of upper/lowercase letters, numbers, and symbols. Disable any legacy or insecure features and restrict admin access to trusted networks.
- Document and verify: Note the reset in your asset management system and verify that the printer now asks for a new password on login. Validate that no default credential remains active.
If you cannot locate the exact steps for your firmware, consult the Epson TM-U220 manual or contact Epson support. Always perform a test print and login verification after a reset to confirm secure operation.
Post-reset hardening: best practices
After resetting, implement a defense-in-depth approach to minimize future risk:
- Use a strong, unique password: Create a password that is long, random, and not reused elsewhere. Consider adopting a password manager to store it securely.
- Disable or restrict remote admin: Turn off or tightly restrict remote administration interfaces (web, FTP, SNMP) to trusted IP ranges only.
- Enable firmware updates: Keep firmware current to patch known vulnerabilities and improve security controls.
- Network segmentation: Place the printer on a dedicated VLAN or subnet separate from sensitive data sources.
- Monitor and log access: Enable logging on the device and feed logs into a centralized security system for anomaly detection.
- Periodic credential review: Schedule regular password reviews and rotate credentials on a defined cadence.
Verification and audit checklist
To ensure ongoing security, perform a quick post-reset audit:
- Confirm password reset was accepted and the old credentials no longer work.
- Validate that login prompts appear only for authorized users.
- Check that print jobs are not accessible via unsecured channels.
- Verify firmware version and enable required security features.
- Create an incident-response plan for lost credentials or suspected compromise.
Common pitfalls and how to avoid them
Many admins trip over similar issues when resetting printers:
- Assuming a universal default exists: Always verify against your specific model/firmware.
- Skipping documentation: Without recording the reset, you risk reintroducing weak credentials later.
- Forgetting to rotate credentials: A reset is not complete if the new password is never used or shared insecurely.
- Ignoring firmware: Outdated firmware leaves known vulnerabilities unpatched.
Long-term security strategy for printers in a small business
A sustainable approach combines technology and process:
- Establish a printer security policy that includes password hygiene, access controls, and change schedules.
- Centralize device management where possible, ensuring consistent configuration across fleets.
- Schedule regular firmware updates and security reviews for critical devices like the TM-U220.
- Train staff to report unusual printer behavior or login prompts immediately to reduce dwell time for attackers.
- Maintain a current asset inventory with firmware versions and security settings to support audits.
Documentation and incident response for printer credentials
Keep a security-ready record of all password changes, device locations, and network role assignments. In the event of a suspected compromise, follow your incident-response plan: isolate affected devices, rotate credentials, collect logs, and coordinate with IT for root-cause analysis. These steps help prevent lateral movement and preserve business continuity.
: {"items":[{"question":"What is the default password for Epson TM-U220?","
Placeholder data table for illustrative purposes
| Name | Value | Unit |
|---|---|---|
| Water usage | 90 | gallons |
| Time | 30 | minutes |
Your Questions Answered
What is the default password for Epson TM-U220?
There is no universal default password that applies to every TM-U220 unit. Default credentials, if present, depend on firmware and model. Always check the official Epson documentation for your exact unit and reset to secure it.
There isn’t a single universal default password for the TM-U220; consult the manual for your exact model and reset to secure it.
How do I reset the Epson TM-U220 to factory defaults?
Enter the printer’s maintenance or recovery mode as described in the manual and select the factory reset option. After reset, immediately reconfigure with a strong password and disable any default credentials.
Use maintenance mode to reset, then set a new password and disable default credentials.
Is it safe to perform a factory reset on a live printer in production?
Factory resetting clears configurations and credentials, which can affect workflows. Perform resets during a planned maintenance window, back up settings where possible, and verify operations afterward.
Only reset during planned maintenance and verify operations after the reset.
How can I prevent default passwords from reappearing after a reset?
Immediately replace the default credentials with strong, unique passwords, disable insecure interfaces, and implement password rotation policies monitored by IT.
Replace defaults with strong passwords and enable rotation policies.
Where can I find official Epson documentation for the TM-U220?
Visit Epson’s official support site and search for TM-U220 manuals and maintenance guides to obtain model-specific reset instructions and security recommendations.
Check the official Epson support site for your model’s manuals.
“Security starts with controlling admin access and rotating credentials across all networked devices, including printers.”
Key Takeaways
- Actionable: Reset default credentials on legacy printers like Epson TM-U220 and secure them immediately
- Be proactive: Disable remote admin interfaces and rotate passwords regularly
- Document changes: Maintain an auditable trail of resets and policy updates
- Security mindset: Treat printers as part of the broader device security posture