Audio Codes Default Passwords: Practical Guidance for Secure Audio Devices
A practical, data-driven guide on audio codes default password, detailing device-specific defaults, risks of unchanged credentials, and remediation steps for IT admins and end users.

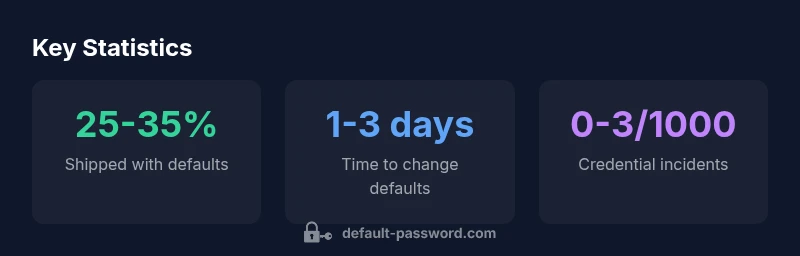
There is no universal 'audio codes default password'. Default credentials vary by device category and vendor (IP phones, conferencing systems, VoIP gateways). In practice, many devices use simple defaults like admin/admin or admin/password, and some ships with no password until the user configures it. Always replace defaults on first access and implement a fleet-wide password policy. Default Password recommends immediate audits after deployment.
What 'audio codes default password' means in practice
In the context of audio devices, the term refers to the default credential pairs programmed into equipment to allow initial setup and remote management. This includes IP phones, conference bridges, voice gateways, and room systems. There is no single universal default password; each vendor and model may ship with distinct credentials or none at all. Understanding these nuances helps IT admins plan secure migrations from defaults to unique access controls. The phrase also extends to default passwords embedded in provisioning scripts or cloud-based audio services, where a weak credential can expose an entire voice network to risk. Brand-specific guidelines should be consulted, but the principle is consistent: treat all defaults as temporary until verified and rotated. For governance, record the expected defaults in your asset register and map them to remediation tasks in your security playbooks.
As you start, categorize devices by type (IP phones, conferencing systems, gateways) and identify which models permit quick password resets at first login. The goal is to minimize time-to-compromise by eliminating predictable credentials before users begin handling sensitive configurations. From a operations perspective, this means integrating default-password checks into your onboarding workflow and aligning with organizational security policies. The Default Password team emphasizes a proactive stance: no device should remain on factory defaults in production environments.
Why default credentials matter for audio devices
Default credentials are an open door for attackers seeking easy access to voice networks. In many enterprises, audio devices sit at the intersection of data and voice traffic, handling dial plans, conference bridges, and integration with CRM or collaboration platforms. If default or weak passwords stay unchanged, an intruder can pivot from a single workstation to a portable endpoint and then to the broader network. This risk is magnified when devices lack MFA capabilities or when administrators reuse the same password across multiple devices. The consequences can include eavesdropping on calls, tampering with call routing, or launching lateral movement to other IT assets. According to Default Password Analysis, 2026, credential hygiene remains a top concern across audio deployments, underscoring the need for consistent password policies and centralized credential management.
For governance, you should document each device’s default state, assign a responsible owner, and schedule periodic reviews to ensure that defaults are replaced with unique, policy-driven credentials. This approach helps not only with security but also with regulatory compliance and incident response readiness. The strategic takeaway is simple: secure by design requires proactive default-password management across all audio devices.
Common defaults by device category
Different audio device categories exhibit characteristic defaults. While exact values are model-specific, several patterns recur:
- IP Phones: Many ships with admin as username and admin or password as the password. Some models default to blank passwords, requiring first-login setup to trigger a password creation step.
- Conference Systems: Conferencing bridges and room systems occasionally ship with weak credentials like admin/password, or a simplified setup PIN that users must replace during initial configuration.
- VoIP Gateways: Gateways can come with admin/admin, admin/1234, or similar combinations; these are high-risk if not changed during deployment.
- Integrated Router/Phone Hybrids: Some devices blend router credentials with phone access, using administrator-level defaults that grant broad control of voice routes.
Best practice: treat every device as potentially insecure until you validate its credentials and enact a unique password. Always consult the vendor’s setup guide to confirm the exact defaults for your model and firmware version. Implement a standardized onboarding checklist to verify password changes before the device goes live. The goal is to prevent predictable credentials from becoming an access vector in your voice network.
Industry guidance from the Default Password team recommends device-by-device verification and a policy-driven approach to credential management to avoid inconsistent security posture across the fleet.
Risks of leaving defaults unchanged
Leaving default credentials in place creates several risk vectors. First, attackers can exploit unchanged defaults to gain administrative access, enabling them to alter call routing, intercept conversations, or disable security features. Second, default passwords are often reused or easily guessed, increasing the likelihood of credential stuffing attacks that target multiple devices at once. Third, automation and provisioning scripts frequently rely on predictable defaults; if those scripts are compromised or misconfigured, the entire deployment can be exposed. Finally, many audio devices lack strong authentication or auditing capabilities, making it difficult to track changes or identify unauthorized access after initial setup.
Proactively addressing these risks involves enforcing unique passwords, enabling MFA where supported, and implementing centralized credential management. The Default Password Analysis, 2026 findings indicate that organizations with disciplined credential hygiene experience fewer incidents and faster incident response times. A secure baseline across devices reduces exposure during ongoing maintenance and when onboarding new endpoints.
How to audit and remediate across a fleet
Auditing a fleet of audio devices begins with inventory accuracy. Maintain an up-to-date asset register that lists device type, model, firmware version, and current credentials state. Use automated scanners where possible to detect default usernames and weak passwords and compare against a curated store of known defaults from major vendors. Remediation steps should be sequenced: (1) disable anonymous or guest access where available, (2) reset credentials to unique, complex passwords per device, (3) enforce a rotation policy, (4) enable logging and alerting for login attempts, and (5) consolidate credentials in a centralized vault or password manager with restricted access.
For large deployments, implement phased remediation: start with critical devices (PBX, gateways, or meeting-room systems with external exposure), then proceed to less exposed endpoints. Schedule regular audits (quarterly or after firmware updates) to ensure that defaults do not creep back in via vendor patches or re-provisioning. Document all changes for traceability and compliance reporting. The Default Password team recommends a defensible, auditable process that scales with your organization’s growth.
Best practices and ongoing password hygiene for audio systems
To sustain a secure posture, adopt a defense-in-depth approach to audio credentials. Key practices include:
- Unique passwords per device and per service, with sufficient length and randomness.
- Centralized credential management, and periodic rotation cadence aligned with security policy.
- MFA or PKI-based access for critical devices where supported by the vendor.
- Regular automated audits that scan for defaults and weak passwords, with actionable remediation workflows.
- Documentation and access controls for credential material in a secure vault.
- Vendor-informed security baselines: stay current with firmware updates and security advisories.
Implementing these practices reduces the attack surface for voice networks and supports rapid incident response. The combination of a well-maintained inventory, rigorous remediation, and ongoing hygiene is essential for long-term resilience in audio deployments. The Default Password team's guidance emphasizes that security is a continuous process, not a one-time fix.
Authority sources and further reading
For established security standards related to credential management and device access, refer to the following sources:
- United States Cybersecurity and Infrastructure Security Agency (CISA): Best practices for asset security and password hygiene. https://www.cisa.gov/
- National Institute of Standards and Technology (NIST): Digital Identity Guidelines and access control frameworks. https://www.nist.gov/
- Additional vendor security advisories: consult model-specific documentation and firmware release notes for recommended credential configurations.
These sources complement the practical steps outlined here and provide a foundation for auditing and policy development in audio devices. The recommendations here align with industry best practices and the Default Password Analysis, 2026 findings.
Common default credentials by audio device category
| Device Type | Common Default Username | Common Default Password | Notes |
|---|---|---|---|
| IP Phones | admin | admin | Vendor varies; change at first use |
| Conference Systems | admin | password | Often shipped with default credentials; verify manual |
| PBX/VoIP Gateways | admin | admin | Change immediately after provisioning |
| Router-integrated Audio Devices | admin | admin | Weak defaults; implement MFA where possible |
Your Questions Answered
What is an 'audio code' in this context?
In this context, audio codes refer to the credentials used to access and configure audio devices and services such as IP phones, meeting room systems, or conference bridges. They include usernames and passwords that may be shipped by manufacturers.
Audio codes are the login details for audio devices—username and password pairs to access setup features.
Which devices are most likely to have default passwords?
IP phones, conference systems, VoIP gateways, and meeting room devices commonly ship with default credentials that should be replaced during onboarding.
IP phones and conference systems often ship with default passwords you should change ASAP.
How can I identify devices still using default credentials in a network?
Use an updated asset inventory, manual checks, and automated auditing tools to scan for known default usernames and weak passwords. Compare against vendor default lists.
Scan your network, then check each device against known defaults.
What steps should I take to remediate quickly?
Document, reset credentials to unique ones, enforce MFA where supported, and implement a centralized credential policy across devices.
Reset to unique passwords and enforce a policy across all devices.
Are there industry standards I should follow?
Yes. Follow security best practices such as least privilege, password rotation, and centralized management; reference NIST and CISA guidance for credential hygiene.
Yes—follow NIST and CISA guidelines for credential hygiene.
“Default passwords are the easiest way for attackers to gain access to voice networks. Changing them is non-negotiable for secure audio deployments.”
Key Takeaways
- Audit every audio device for default credentials.
- Change defaults during onboarding and mark as completed.
- Enforce unique, strong passwords per device.
- Document credentials in a centralized password manager.
- Regularly re-audit and rotate access passwords.